
Laptop & Mobile Device Risks, Mitigation In The Health Care Industry
March 12th, 2016
Mike Jann of medical IT support management firm Medicus Solutions analyzes the impact of inefficient security in your health care organization and what your company can do to combat it.
Alpharetta, GA – With the details and implications of the PRISM program now public and recent events between Apple and the FBI hot topics around water coolers across the country, the presence of privacy and the security of data is in the news more than ever before. Now a new report from California Attorney General Kamala Harris[1] has exposed startling and consistent weaknesses among health care organizations’ security. Jann’s experience confirms the report’s summary: Health care organizations must do a better job at securing sensitive patient from malware and hacking, physical breaches, and errors that result in breaches. Find out how to help your organization avoid a breech that could sink your company.
Scope of the Health Care Security Challenge: By The Numbers.
- The records for 24 million residents in a single state were breached according to the report, representing a nearly 6x increase in a single year.
- 55% of compromised records in the health care sector were the result of a failure to encrypt data.
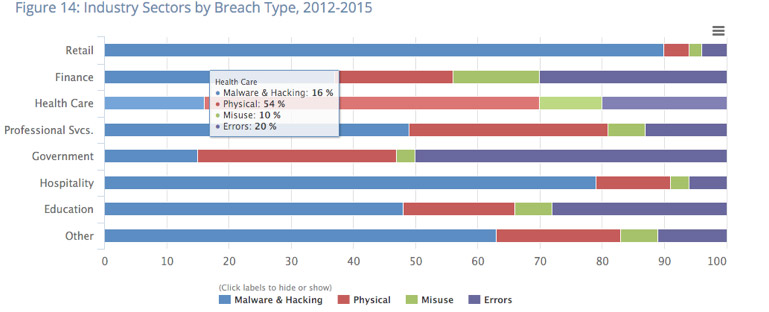
- Roughly 50% of health care breaches came secondary to lost or stolen equipment, typically laptops.
- Hacking remains a major threat to security of sensitive data, including social security numbers and medical records. Malware and hacking breaches are on the rise as electronic medical record systems grow in popularity.
- Small businesses remain the most susceptible to hacking and malware attacks, as well as breaches due to physical loss. The medical industry has the highest percent of breaches due to physical loss.
Source: California Data Breach Report, February 2016
The Real Costs to Data Breaches Health Care Entities & Individuals
The significance and impact of these data breaches on both individuals and medical practices cannot be understated. For practices, data breaches not only impose financial, reputational, business opportunity penalties and costs, they also threaten critical infrastructure. For the individual, the impact hits closer to home: research from Javelin Strategy & Research[2] notes that 67% of victims of data breaches are also victims of fraud. The stakes are high for all parties involved and the need for strong security couldn’t be higher. On May 5, 2015, UCLA Health concluded that a hacker accessed parts of their network that contained the addresses, DOB’s, social security numbers and medical records of 4.5 million individuals. The data was not encrypted[3].
Mobile Device & Laptop Security In Health Care – The Biggest Threat
Security breaches resulting from the theft or loss of unencrypted devices represents one of the single biggest threats to the health care sector. In fact, physical breaches represent more than half of all security breaches in this sector according to the report, accounting for 2.8 million records breached in one state alone. “A large part of these losses came from data stored on laptops and USB drives,” Jann said. “Mobility coupled with a lack of security have resulted in some of the biggest breaches we’ve seen to date and remains a huge threat to small business in particular, as they tend to not have robust security features installed.”
What Your Health Care Organization Can Do To Better Protect Data On Mobile Devices.
- Implement proper security protocols in your organization. With hackers breaking into healthcare networks, hackers can’t be allowed to access sensitive unencrypted data. The first goal should be to make sure that your organization is functioning within NIST’s guidelines for encryption compliance. There is an important “safe harbor” provision written into the 2009 HITECH Act’s interim final breach notification rule[4] where if your company experiences a breach that affects more than 500 people, you can be exempt from reporting the incident if your encryption falls within those required guidelines.
- Analyze the environment to understand breach risks. By reviewing the life cycle of how data enters and exists your companies walls, you gives your IT professionals the opportunity to identify the weakest points in the security of the organization and form strategies to address them before problems occur. Do you know what your users are doing with laptops that have access to sensitive information on and off company premises?
- Evaluate enterprise security controls and encryption needs. Not everyone needs access to every sensitive document and folder. Identify who needs access to what and encrypt files and folders as needed.
- Implement stronger security for your cloud-stored data. Most cloud services used by health care organizations are often times not thoroughly vetted for proper security before being used. Cloud storage data breaches can happen and when they do, it is essential that your organization’s data is safe.
- Staff education. Training staff to understand and be disciplined in its use of security protocols is essential to any effective security system. Make sure your personnel understands the necessity to follow all rules and regulations set forth by your IT team and commits to following them fully.
At Medicus, Jann and his team use WinMagic[5] (http://www.winmagic.com) and recommend it to their medical IT clients as the preferred method of securing sensitive files on laptops and mobile devices. “This service gives medical IT administrators centralized control over all encryption keys for the entire practice, including multiple locations, removing that responsibility from the cloud providers and giving it back to your practice where it belongs,” urges Jann. “In short, it ensures that all files are encrypted on the mobile or desktop device before ever being moved to the cloud, thus eliminating the risk of data breaches on the laptop/mobile device or in the cloud. Without the encryption key, data on said devices or cloud services would be useless to hackers. We highly recommend it.”
No matter what service you decide to use, the important take-away is that your health care organization implement essential encryption systems to keep your sensitive data safe. For devices that represent a natural threat for physical loss like laptops, implementing encryption of work-related folders, developing and implementing a security plan, and educating staff in the proper use of said systems are essential to bullet-proof security. For implementation, support, and related services, our team at Medicus Solutions is ready to assist your organization and maximize its security potential. We can quickly evaluate the quality of your current security solutions, test your backups and networks, scan or vulnerabilities, implement new secure systems and services, and much more. If your organization would like a full evaluation from a team with more than 20 years of experience in IT security services, we encourage you to contact us today.
—
About Medicus Solutions:
Medicus Solutions, LLC (http://162.241.140.166/~msinc/) is an Alpharetta, GA based company that specializes in providing medical IT support management to improve the efficiency, security and stability of your company’s operations. Medicus offers a range of IT services that work both independently and in unison to ensure your company operates securely, seamlessly and efficiently. Featuring secure email and backup services, virtual hosting services, HIPAA-approved file encryption systems, and much more. For more information about Medicus Solutions, please call our main offices in Alpharetta at 678-495-5900 or visit us at our website.
Medicus Solutions writes about news, technologies, and educational topics that are defining the future of health care IT solutions and security issues at its blog: http://162.241.140.166/~msinc/blog/
Source: Medicus Solutions, LLC.
###
[1] http://www.hhs.gov/hipaa/for-professionals/breach-notification/laws-regulations…
[2] http://www.winmagic.com/products/cloud-file-encryption-software-key-management
[3] https://www.javelinstrategy.com/fraud-and-security
[4] http://www.latimes.com/business/la-fi-ucla-medical-data-20150717-story.html
[5] https://oag.ca.gov/breachreport2016
Categories
Archives
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 | 31 | ||